Improve your risk posture with attack surface management
Security that enables business outcomes AC Motor

Gain visibility and meet business needs with security
Connect with confidence from anywhere, on any device
Secure users and key operations throughout your environment
Move faster than your adversaries with powerful purpose-built XDR, attack surface risk management, and zero trust capabilities
Maximize effectiveness with proactive risk reduction and managed services
Understand your attack surface, assess your risk in real time, and adjust policies across network, workloads, and devices from a single console
Drive business value with measurable cybersecurity outcomes
Evolve your security to mitigate threats quickly and effectively
Ensure code runs only as intended
Gain visibility and control with security designed for cloud environments
Protect patient data, devices, and networks while meeting regulations
Protecting your factory environments – from traditional devices to state-of-the-art infrastructures
ICS/OT Security for the oil and gas utility industry
ICS/OT Security for the electric utility
Stop threats with comprehensive, set-it-and-forget-it protection
Bridge threat protection and cyber risk management
Your generative AI cybersecurity assistant
Stop breaches before they happen
Stop adversaries faster with a broader perspective and better context to hunt, detect, investigate, and respond to threats from a single platform
The most trusted cloud security platform for developers, security teams, and businesses
Cloud asset discovery, vulnerability prioritization, Cloud Security Posture Management, and Attack Surface Management all in one
Extend visibility to the cloud and streamline SOC investigations
Secure your data center, cloud, and containers without compromising performance by leveraging a cloud security platform with CNAPP capabilities
Simplify security for your cloud-native applications with advanced container image scanning, policy-based admission control, and container runtime protection
Security for cloud file/object storage services leveraging cloud-native application architectures
Defend the endpoint through every stage of an attack
Stop adversaries faster with a broader perspective and better context to hunt, detect, investigate, and respond to threats from a single platform
Optimized prevention, detection, and response for endpoints, servers, and cloud workloads
On-premises and cloud protection against malware, malicious applications, and other mobile threats
Expand the power of XDR with network detection and response
Stop adversaries faster with a broader perspective and better context to hunt, detect, investigate, and respond to threats from a single platform
Protect against known, unknown, and undisclosed vulnerabilities in your network
Detect and respond to targeted attacks moving inbound, outbound, and laterally
Redefine trust and secure digital transformation with continuous risk assessments
Stop phishing, malware, ransomware, fraud, and targeted attacks from infiltrating your enterprise
Stop phishing, ransomware, and targeted attacks on any email service including Microsoft 365 and Google Workspace
Learn about solutions for ICS / OT security.
Stop adversaries faster with a broader perspective and better context to hunt, detect, investigate, and respond to threats from a single platform
Keep ahead of the latest threats and protect your critical data with ongoing threat prevention and analysis
Augment security teams with 24/7/365 managed detection, response, and support
Augment threat detection with expertly managed detection and response (MDR) for email, endpoints, servers, cloud workloads, and networks
Our trusted experts are on call whether you're experiencing a breach or looking to proactively improve your IR plans
Stop breaches with the best response and detection technology on the market and reduce clients’ downtime and claim costs
Grow your business and protect your customers with the best-in-class complete, multilayered security
Deliver modern security operations services with our industry-leading XDR
Partner with a leading expert in cybersecurity, leverage proven solutions designed for MSPs
Add market-leading security to your cloud service offerings – no matter which platform you use
Increase revenue with industry-leading security
We work with the best to help you optimize performance and value
In-depth insights and protection strategies >
Content has been added to your Folio
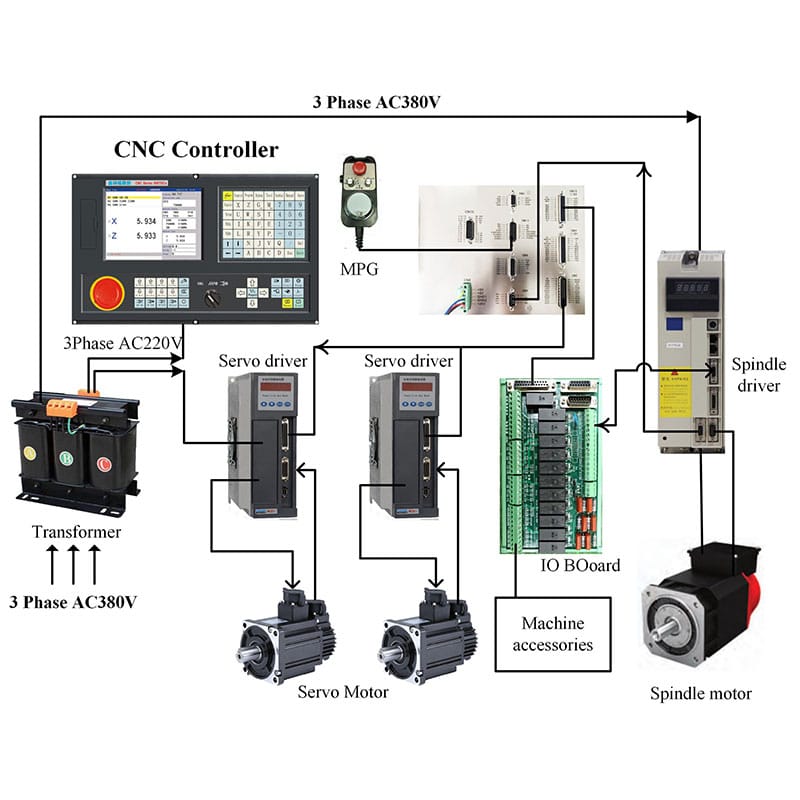
This three-part blog series explores the risks associated with CNC machines
By: Trend Micro December 01, 2022 Read time: ( words)
In part one, we discussed what numerical control machines do and their basic concepts. These concepts are important to understand the machines better, offering a wider view of their operations. We also laid out how we evaluated the chosen vendors for our research.
For this blog, we will continue discussing our evaluated vendors and highlighting findings that we discovered during our research.
Haas was the first vendor we focused on because of the fast availability of its controller. We began our analysis by conducting port scanning on the controller simulator and identifying the protocols exposed by the controller. After that, we evaluated the options with which an attacker could abuse the protocols to perform attacks aimed at the security of the machine and verified these attacks in practice on a real-world machine installation.
Okuma stands out in the market of CNC controllers for one interesting feature: the modularity of its controller. While the vendor offers in the device’s simplest form a tiny controller, it also provides a mechanism, called THINC API, to highly customize the functionalities of the controller. With this technology, any developer can implement a program that, once installed, runs in the context of the controller, in the form of an extension. This approach is very similar to how a mobile application, once installed, can extend a smartphone’s functionalities.
In the spirit of the Industry 4.0 paradigm, Heidenhain offers the Heidenhain DNC interface to integrate machines on modern, digital shop floors. Among the many scenarios, Heidenhain DNC enables the automatic exchange of data with machine and production data acquisition (MDA/PDA) systems, higher level enterprise resource planning (ERP) and manufacturing execution systems (MESs), inventory management systems, computer-aided design and manufacturing (CAD/CAM) systems, production activity control systems, simulation tools, and tool management systems
In our evaluation, we had access to the library provided by Heidenhain to the integrators to develop interfaces for the controller. The manufacturer provides this library, called RemoTools SDK,35 to selected partners only.
Like Heidenhain, Fanuc offers an interface, called FOCAS,36 for the integration of CNC machines in smart network environments. Even though this technology offers a restricted set of remote-call possibilities compared with the other vendors’ (that is, a limited number of management features), our experiments showed that a miscreant could potentially conduct attacks like damage, DoS, and hijacking.
As our evaluation identified 18 different attacks (or variations), we grouped them into five classes: compromise, damage, and denial of service (DoS):
Controller manufacturers like Haas, Okuma, and Heidenhain have been found to have a similar number of issues, around 15. Fanuc had 10 confirmed attacks. Unfortunately, our research shows that this domain lacks awareness concerning security and privacy. This creates serious and compelling problems.
The need for automation-facing features like remote configuration of tool geometry or parametric programming with values determined by networked resources is becoming more common in manufacturing.
With these findings, we determined countermeasures that enterprises can do to mitigate such risks, which we’ll discuss in our final installation. In the last part, we’ll also discuss our responsible disclosure process.
Try our services free for 30 days
Privacy | Legal | Accessibility | Site map
1000 Series Controller Copyright ©2024 Trend Micro Incorporated. All rights reserved